How to use WPA2 for wireless network security?

Network security technologies are improving every hour. Protection of the system from hackers and other security threats is essential because they are faced daily. WPA2 is a network security version which is advanced version of WEP (Wired Equivalent Privacy) and WAP. It uses the IEEE 802.11 technology standard for encrypting data. It is used on all Wi-Fi hardware since 2006. The improved security is because of the strong encryption techniques.
Encryption Techniques
WPA 2 is expanded as Wi-Fi Protected Access version 2 (WPA2). It is an enhanced protected version of WPA because it uses the Advanced Encryption Standard (AES) for encryption. There are two kinds of protection methodology by WPA2, they are:
- WPA2 with AES and
- WPA2 with AES and TKIP.
In the later Temporal Key Integrity Protocol (TKIP) along with AES has to be enabled by the router. The security provided by WPA2 is a ‘top-secret grade’ of security which is used by the government. This level of security is achieved by using the National Institute of Standards and Technology (NIST) FIPS 140-2 compliant AES encryption algorithm and 802.1x-based authentication.
WPA2 Versions
It has two versions, one is called WPA2 Enterprise, which verifies network through a server and the other is called WPA2 Personal, which uses a password-based protection technique. WPA2 PSK (Pre-shared Key), is designed especially for home users because they do not require an enterprise authentication key. 8 to 63 characters long and plain-English paraphrase is used as a password, instead of an encryption key to the router. TKIP along with network SSID uses that paraphrase to generate a unique id to connect with each wireless client. These unique keys are often changed to ensure security and they are 0-9 and A-F hexadecimal codes.
Setting Up a WPA2 Router
After plugging the necessary cables and powering on the router, wait for the network signals. The internet connectivity and the router connectivity are indicated by the LEDs provided in the modem kit.
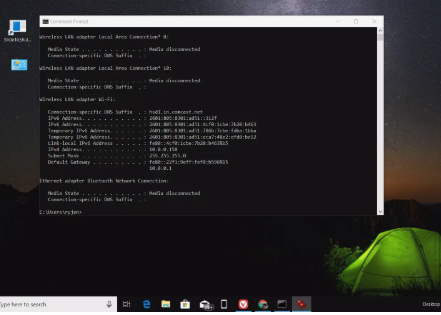
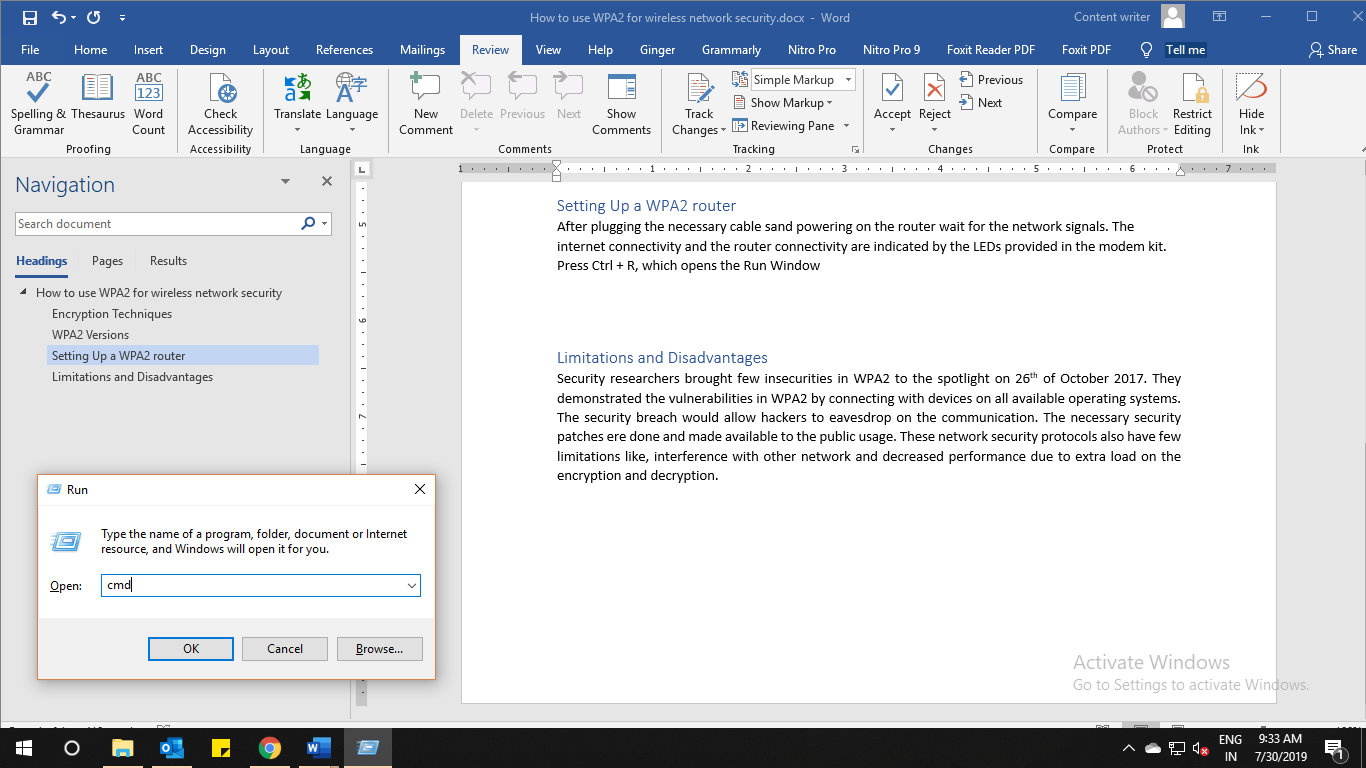 Press Ctrl + R, which opens the Run Window and type CMD as shown in the figure. It opens a command prompt, in which type the command ipconfig as shown below:
Press Ctrl + R, which opens the Run Window and type CMD as shown in the figure. It opens a command prompt, in which type the command ipconfig as shown below:
Open the browser and type the IP listed in the window which opens the Default Gateway. Wi-Fi SSID and the Wi-Fi passkey are seen on the router window. Set up your passkey and connect to any device like laptop, mobile and tablet, etc.. If you are connecting for the first time, please type your password to connect. Therefore, once the connection is established, then your connection status is changed as connected.
Limitations and Disadvantages
Security researchers brought few insecurities in WPA2 to the spotlight in 2017. They demonstrated the vulnerabilities in WPA2 by connecting it with devices on all available operating systems. The security breach would allow hackers to eavesdrop on communication. The necessary security patches are available to public usage, immediately after fixing. These network security protocols also have few limitations like interference with another network. Therefore the decreased performance is because of the extra load on the encryption and decryption.
Recommended Posts

Top 5 Free WooCommerce Extensions for Boosting Sales
February 3, 2023

Top 5 WordPress Security Mistakes and How to Fix Them
January 25, 2023

6 Must-Know WordPress Plugins for SEO
January 6, 2023
